Description
In this course, you will :
- In the first week you’ll be able to discuss the basics of deterrents and how to “trick” attackers into believing they’ve hit a goldmine of data away from your real systems.
- In week 2, you’ll be able to understand and discuss the steps of penetration testing methodology.
- In week 3, you will be able to understand and apply what you have learned on your own systems to test whether your systems are secure or not.
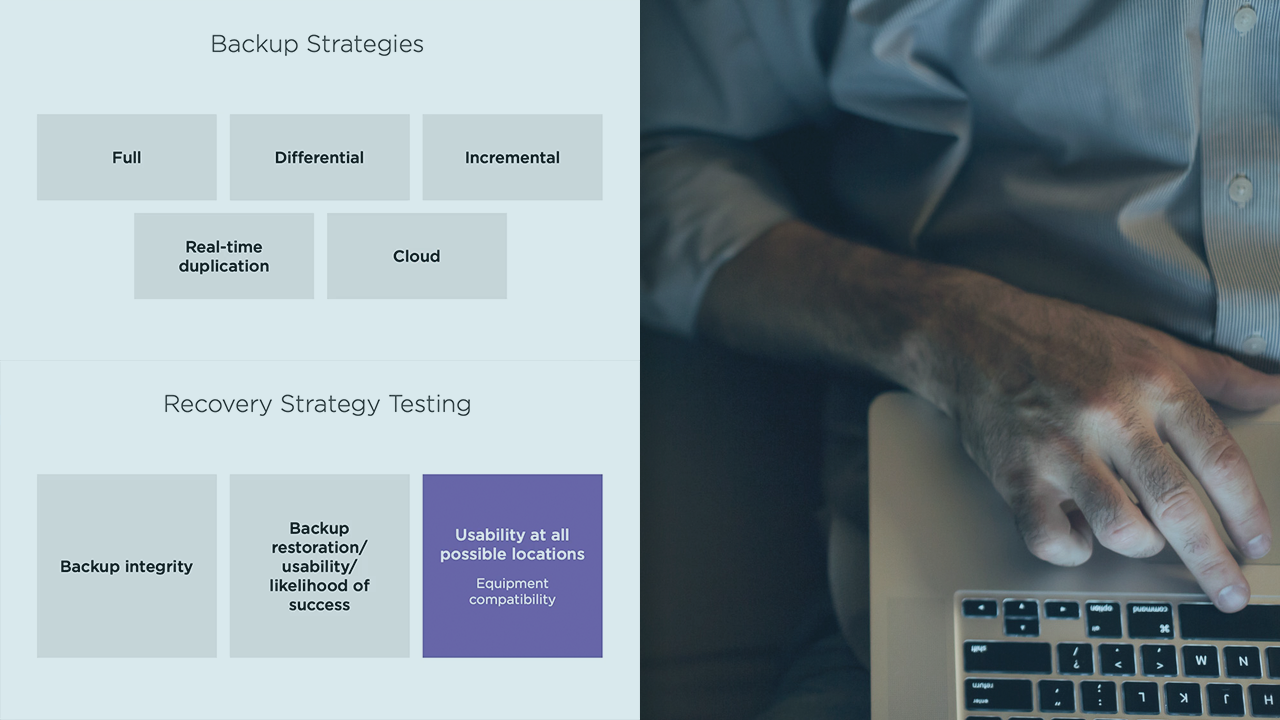
- In week 4, we’ll discuss planning for your own methodology that you can apply to your own systems.
- in week 5, we’ll finish up with a project that will allow you to test your skills in a safe environment.