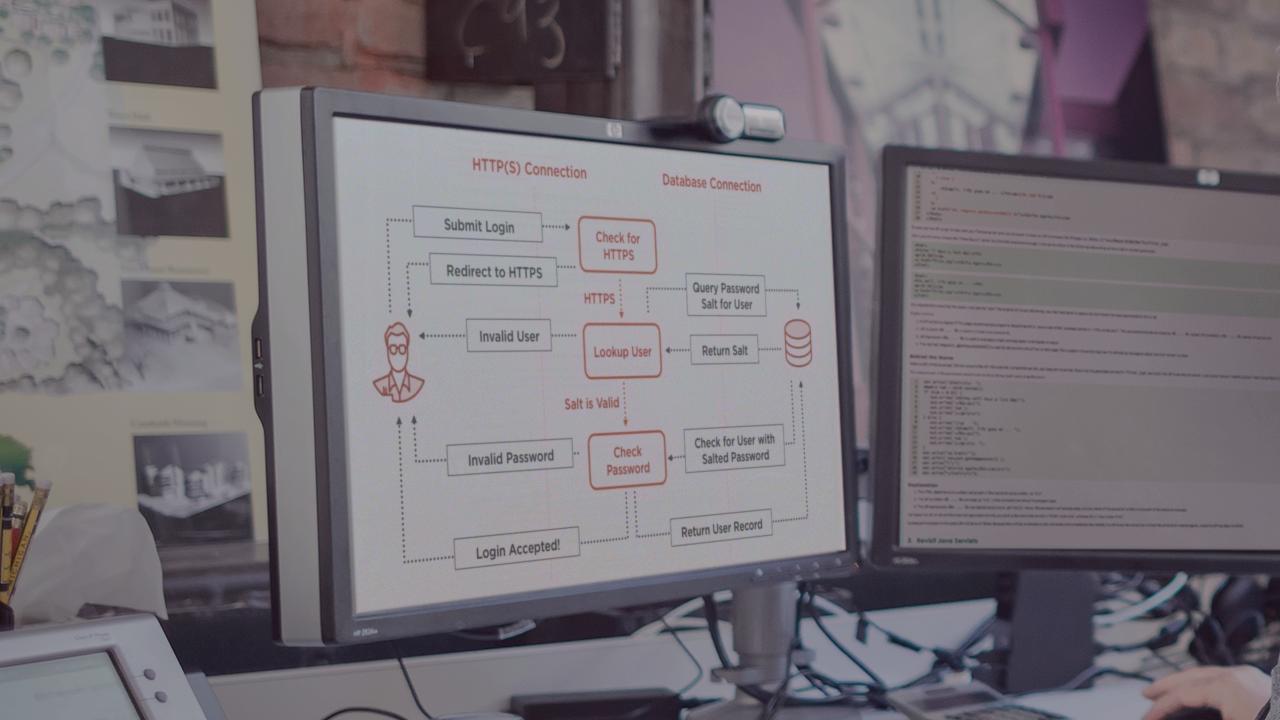
Description
In this course, you will :
- This course looks at detection and mitigation of threats and attack vectors and discusses how to use tools and principles to protect information.
- By the end of the course you should be able to make suggestions on what type of detection and mitigation strategy is right for your systems or business given the known threats and attack vectors.
- You should be able to discuss what features you want in a firewall, or how cash registers or sensitive data systems should be secured.